Hello dear readers, it has been a while since I posted an article on here. But having temporarily finished work on something relating to data security, I figured I would write an article on the topic.
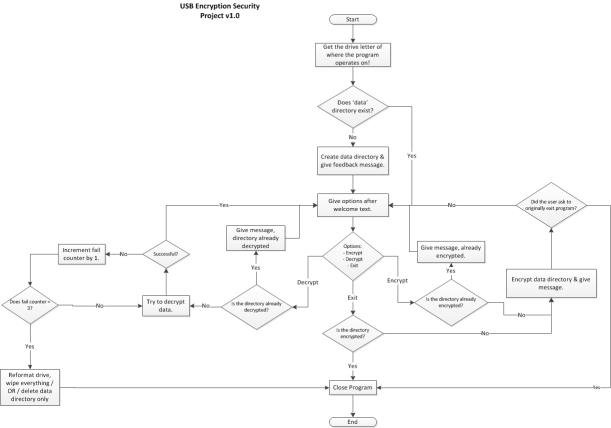
Recently I finished working on the base version of a personal project I took up that deals in data encryption. Descriptions about that project can be found here. Working on this project required quite a lot of research on my part in terms of hashing, encryption and some other aspects of the programming language I chose to use. As a part of my research, it became even more clear just how important data security is.
I am going to recount a personal experience of mine as to what got me into this data encryption project of mine. Sometime in January 2018, I was looking for one of my USBs (one that I tend to use a lot) and could not find it. It worried me a little as I very rarely lose things. I recounted my steps to every location I could think of having been to, and searched for the USB with no success. Ironically enough, I had nearly given up on it, but then I stumbled upon it in a very well hidden pocket of my bag (which I had put it in there myself). I kept it in that pocket to ensure its not as easily discovered, and I myself could not find it…that pocket worked out well I would say.
 Jokes aside though, it made me think about what if I had REALLY lost the USB and it contained sensitive data on it. Someone could easily pick it up, attach it to a computer and browse it’s contents out of curiosity perhaps. That gave me the motivation to work on the encryption project (details about the project can be found here).
Jokes aside though, it made me think about what if I had REALLY lost the USB and it contained sensitive data on it. Someone could easily pick it up, attach it to a computer and browse it’s contents out of curiosity perhaps. That gave me the motivation to work on the encryption project (details about the project can be found here).
With story time out of the way, let’s discuss why data security is important to consider:
-
- We live in a very digital world, everything we do is connected in some shape or form. With the benefits it brings, it also brings downsides. Cyberspace can be a very vulnerable place.
- Cyber warfare is a very real thing. It has been happening for years. But even to just the general public, there are so many ways harm can come to them. For example, malware, adware or spyware products that could plant a back door into your computer to feed information to an outside listener.
- Today’s world is data driven. Almost everything is digitized, at least in the Western sphere. The phrase “money is power” can easily apply to data as well. Data is power. Any sensitive data about you falling into the wrong hands could bring harm to you.
Do you have more reasons you want to share? Please do so!
Reasons to consider encryption:
- When implemented properly, it can be a very STRONG defense mechanism against any prying eyes.
- It’s an added layer of security on top of your anti-virus or any other security software on your computer.
- Encryption has been a proven technique of security for centuries. That does not mean that encryption cannot be cracked, DES for example was cracked all the way back into the 1980’s (perhaps even earlier). Currently AES-256 bit is a good algorithm to use, RSA seems to be the best according to my research, but slow. Although AES-256 can be cracked as well, but the resources required are immense.
- In the case of businesses, it helps to maintain public trust. No client would want to give their information to a business if they know that their data would be vulnerable.
- Even if files were to be taken off a computer, as long as they are encrypted, they are useless without the encryption key to decrypt them with in most cases.
- Encryption for data traveling over the network ensures that any network packets intercepted mid-way would end up essentially being useless to any malicious entity doing reconnaissance or data interception.
Do you have any more reasons you want to share? Please do so!
That’s my quick piece on data security and encryption. I realize there are many articles about this very topic out on the vast land of the internet, but I hope that you were able to learn something along the way perhaps or even have something new to ponder about.
Until next time!
~ Monty




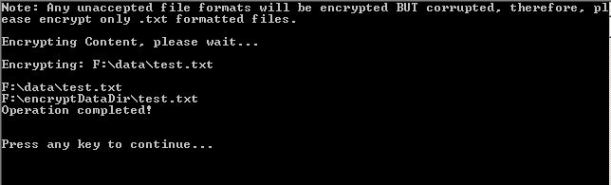

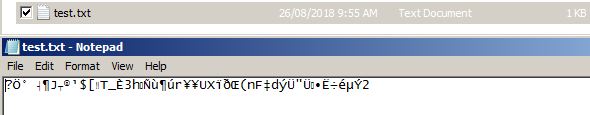
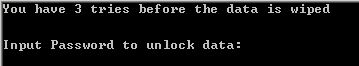
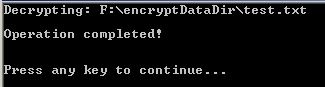








 Type: Fanfiction
Type: Fanfiction
 Type: Fanfiction
Type: Fanfiction